Acronis Cyber Protect Cloud
All-in-one integrated backup and cybersecurity platform for MSPs
Overview:
Easily scale cyber protection services from a single platform – while efficiently running your MSP business
With Acronis Cyber Protect Cloud, you can deliver integrated backup, disaster recovery, cybersecurity, and endpoint management at scale, while preserving your margins and streamlining your business operations with powerful automation capabilities and broad integrations.
Expand your services with advanced protection packs
Add other powerful components to strengthen your services even further with advanced protection packs and unique cyber protection capabilities. Control your costs by paying only for the functionalities your clients need.
Advanced packs include:

Security + XDR
Instead of counting on a costly and complex stack of point solutions, Acronis XDR introduces natively integrated, highly efficient protection built for MSPs:
- Natively integrated cybersecurity, data protection and endpoint management
- Highly efficient security designed to protect the most vulnerable attack surfaces with AI-guided incident analysis and single-click response
- Built for MSPs, including a single agent and console for all services

Security + EDR
Instead of counting on a costly & complex stack of point solutions, Acronis enables MSPs via integration of EDR, endpoint management, and backup & recovery to:
- Easily launch a complete security solution, including rapid recovery
- Protect against modern threats and readily comply with cyber insurance requirements
- Maximize efficiency through a single security platform

Management
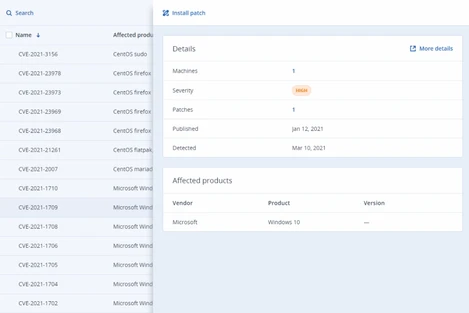
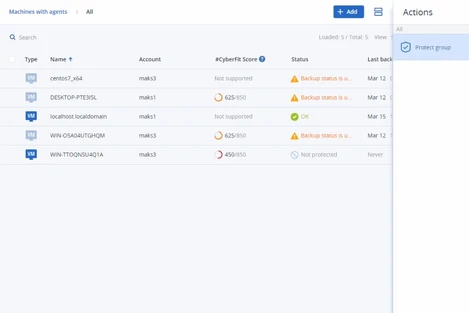
Streamline and automate your routine tasks via scripting and promptly close security gaps in clients’ infrastructure through patch management. Gain visibility into your clients’ software assets and data protection to ease daily tracking and planning tasks, and improve clients’ uptime by monitoring disk drives health.
- Cyber scripting
- Automated patch management
- Disk drive health monitor

Automation
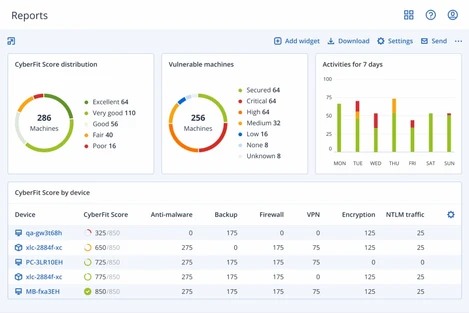
Streamline MSP business with a single integrated platform that automates workflows, improves customer interactions, and provides real-time business insights. Enable data-driven decisions and smarter resource utilization, resulting in improved manageability and value-based client relationships.
- High-performance automation
- Precise forecasting
- Next-level profitability

Advanced Backup
Defend clients’ data, even between scheduled backups. Extend backup capabilities to SAP HANA, Oracle DB, MariaDB, MySQL, and application clusters. You can also gain visibility into data-protection statuses across your clients’ infrastructure.
- Continuous data protection
- Data protection map
- Off-host data processing

Disaster Recovery
Get clients back to business in mere minutes when disaster strikes by spinning up their systems in the Acronis Cloud and restoring them anywhere, ensuring immediate data availability. Make disaster recovery painless and increase efficiency with orchestration, runbooks, and automatic failover.
- Disaster recovery orchestration
- Production failover
- Site-to-site VPN

Email Security
Block any email threat, including spam, phishing, business email compromise (BEC), account takeover (ATO), advanced persistent threats (APTs), and zero days in seconds before it reaches end users. Leverage Perception Point’s next-generation technology for lightning-fast detection and easy deployment, configuration, and management.
- Anti-phishing and anti-spoofing engines
- Anti-evasion and account takeover protection
- Next-generation dynamic detection against zero-days

Data Loss Prevention (DLP)
Prevent leakage of sensitive data from endpoints via more than 70 local and network channels and strengthen compliance with minimal effort and speed to value.
- Content-aware data loss prevention
- Automatic client-specific DLP policy creation and extension
- Pre-build data classifiers for common regulatory frameworks
Why Acronis Cyber Protect Cloud
![]()
Increased Control
Reduce complexity and control the services you deliver for your customers: security, backup, disaster recovery, endpoint management, automation. All with the flick of a switch.
![]()
Vendor Consolidation
Managing multiple vendors leads to increased costs, greater risk, and added operational overhead. Consolidate your vendors and increase efficiency of service delivery to your clients.
![]()
Centralized Management & Monitoring
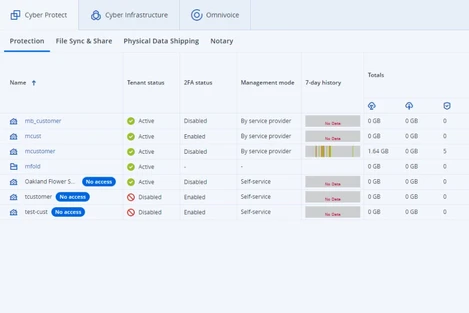
Efficiently manage and monitor your clients through a single console, giving you better and more effective control over their cyber protection.
![]()
World Class Partner Support
Drive your business with pre-packaged marketing campaigns, training, and other resources, available through the Acronis Partner Portal.
![]()
Reduced Training Time
By delivering client services through a single console, you can reduce training time for new technicians by up to 50%, and allow them to focus more time on driving business.
- Pricing and product availability subject to change without notice.
- This product is available as instant electronic delivery upon purchase.
- Acronis Advantage Premier - Offers 24 x 7 support services available via phone, chat, and email. Acronis Advantage Premier customers receive priority support in the event of a business-critical system error (severity A), customers will receive the initial response within one hour. The first year of service is included with the Acronis line of corporate products.